Some links at first as always:
- Sooo useful repo with tools
- You can download Red Star 2 here
- And Red Star 3 here
- And read some staff how intranet works in North Korea
- Files from this article will be uploaded to my TG channel
- Funny review video about Red Star OS
Well, some time ago I made a forensics task for one of the CTF’s that we had in our university. And in that task I used Red Star OS, but didn’t mention the depth of it for researching. I mean they have their own browser, their own root “bypass” tool and much much more
So now, as I don’t have a full-time job, I do have time for such a geek staff :)
Some entering info:
There are 4 versions of Red Star OS(RS further in the text):
- Version 1.0/Beta - 2008 [leaked]
- Version 2.0 - 2009 [leaked]
- Version 3.0 - 2012 [leaked]
- Version 4.0 - 2019 [unleaked]
So our research will be focused on the third version
Some tips and hacks will be taken from rutracker, that I linked above
For me I was able to install it just with VMWare (hacks from rutracker for virtualbox didn’t work for me)
rootsetting
First thing to do after the installation is, obviously, get the root :)
And good-natured korean programmers left a tool for us. It’s rootsetting - 753bd4ccdc4dddc8efe8f0eb4a46e837a6e1de0a
I didn’t find any info in the internet about it, it’s hash on VirusTotal was also absent. But we can find a lot of interesting strings about who has developed it:
(c) 2002,2003 KCC OIC
rootsetting
mirae@osd.inf.kp
Maintainer - Kim Gyong Hun
application for the root settings
Application is being started at account of kcontroltray
It’s a pretty simple program made with Qt and QWidget. It doesn’t have SUID bit, it’s owned by root, so it just changes root password in shadow file
Didn’t reverse it a lot, but looks like it wasn’t necessary: admin_writeShadowFile
We can also predict, that this soft was really written by Kim Gyong Hun, because what does this line really mean You cannot the root disable! :))))
Language
Well, next we’d like to change interface language, easy:
sudo sed -i 's/ko_KP/en_US/g' /etc/sysconfig/i18n
sudo sed -i 's/ko_KP/en_US/g' /usr/share/config/kdeglobals
Whoo!
Now, let’s look around
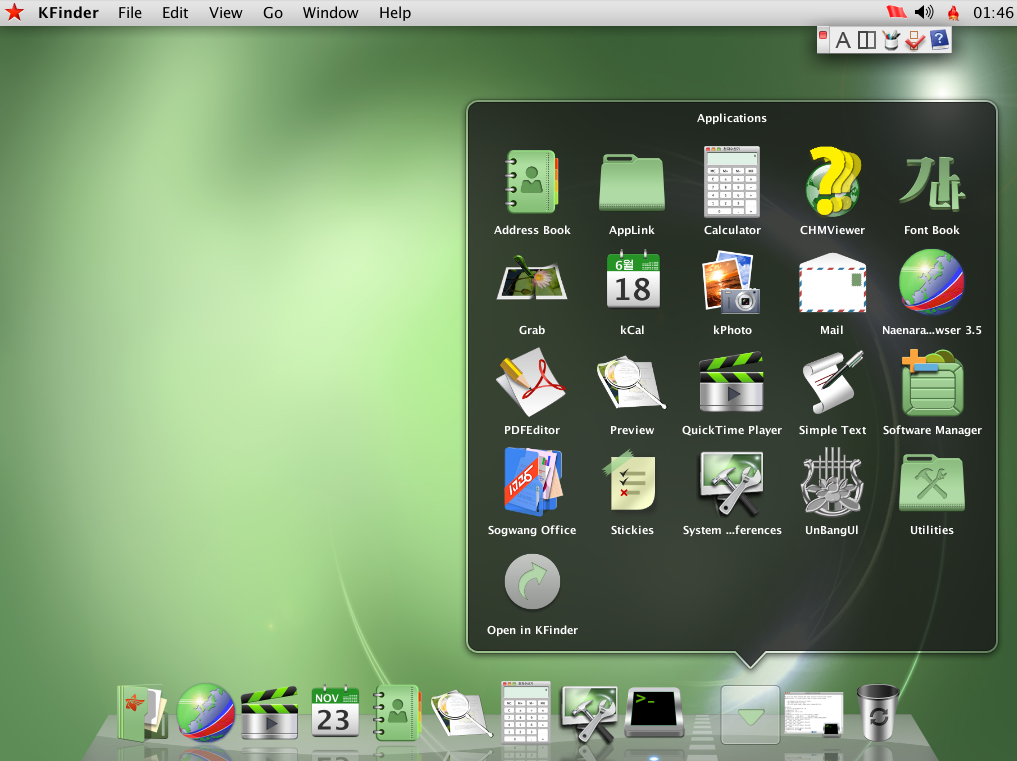
Browser!
Browser
Naenara, when it starts, is trying to connect to 10.76.1.11
From ome of the hackadays we have:
Upon start-up, the browser tries to load a page located at IP address 10.76.1.11, which is a reserved IP address for private use. This indicated that North Korea’s “Internet” is actually more of in intranet. [Robert] suspects that the entire country may be running in private address space, similar to how your home or business likely runs.
All the certs, that I extracted will also be in the channel, but nothing special there, as an example:
Issued To:
CN: GovRSA01
O : GovCA
Issued By:
CN: RootRSA01
O : RootCA
Issued On 2010 09 29
Expired On 2015 09 28
Wandering a bit through browser files we have:
naenara - 6f14260ee9fb054ccd4036f2efdfd1ef4746b180
It’s a binary file, but looks like it just execv’s /Applications/Naenara.app/Contents/RedStar/nnrbrowser
nnrbrowser - f7877b7c7e04523fd656477c507a8679accdc693
SH script to run firefox from 00’s
iptables:
They also have snort preinstalled :)
Rules for iptables look like this:
# Generated by iptables-save v1.4.7 on Fri Apr 13 08:55:11 2012
*filter
:INPUT DROP [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:APPLICATION_FILTER - [0:0]
:INTRUSION_PREVENTION_FILTER - [0:0]
:USER_DEFINED_FILTER - [0:0]
-A INPUT -i lo -j ACCEPT
-A INPUT -j INTRUSION_PREVENTION_FILTER
-A INPUT -j APPLICATION_FILTER
-A INPUT -j USER_DEFINED_FILTER
-A OUTPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 22 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 22 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 80 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 80 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 443 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 443 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 5900 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 5900 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 631 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 631 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 135 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 135 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 137 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 137 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 137 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 137 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 138 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 138 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 139 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 139 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 445 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 445 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 445 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 445 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 20 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 20 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 21 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 21 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 548 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 548 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 1:65535 --dport 5353 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 1:65535 --dport 5353 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 22 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 22 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 80 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 80 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 443 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 443 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 5900 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 5900 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 631 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 631 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 135 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 135 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 138 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 138 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 139 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 139 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 20 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 20 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 21 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 21 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 548 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 548 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p tcp -m tcp --sport 5353 --dport 1:65535 -j ACCEPT
-A APPLICATION_FILTER -p udp -m udp --sport 5353 --dport 1:65535 -j ACCEPT
COMMIT
# Completed on Fri Apr 13 08:55:11 2012